Strong Customer Authentication (SCA) is a cornerstone of secure and seamless digital interactions, ensuring compliance and building trust in today’s online ecosystem. However, the path to implementing SCA varies significantly, and the approach you choose can have far-reaching implications for your organization.
This page examines the differences between two key strategies: developing and implementing an SCA solution internally versus selecting our dedicated, ready-to-use solution. Whether you’re a CTO aiming for strategic alignment, a developer concerned with integration and scalability, or a product manager focused on delivering a user-friendly experience, we’ll guide you through the pros, cons, and practicalities of each option.
Discover which approach best suits your business objectives and operational priorities.
Implementing SCA on your own
Each BaaS partner is presented with general SCA requirements that can be found here, flexibility how to implement it is the key benefit. Nevertheless, additional challenges might be met in such cases when SCA is introduced after all other flows are implemented. In the picture below you can see high-level steps for one of use cases that required SCA.
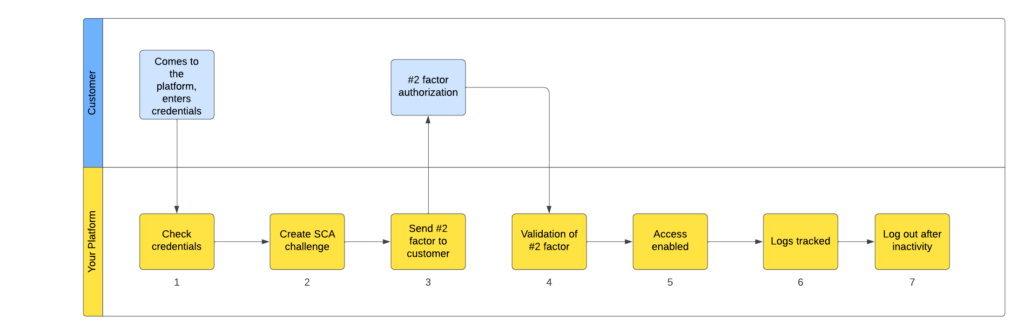
Implementing ConnectPay’s integrated SCA
If Partner sees too many challenges for implementing SCA on their own, alternative approach can be selected – trusting us not only as Embedded Finance provider, but also as SCA provider as well. In the picture below you can see high-level steps for one of use cases that required SCA.
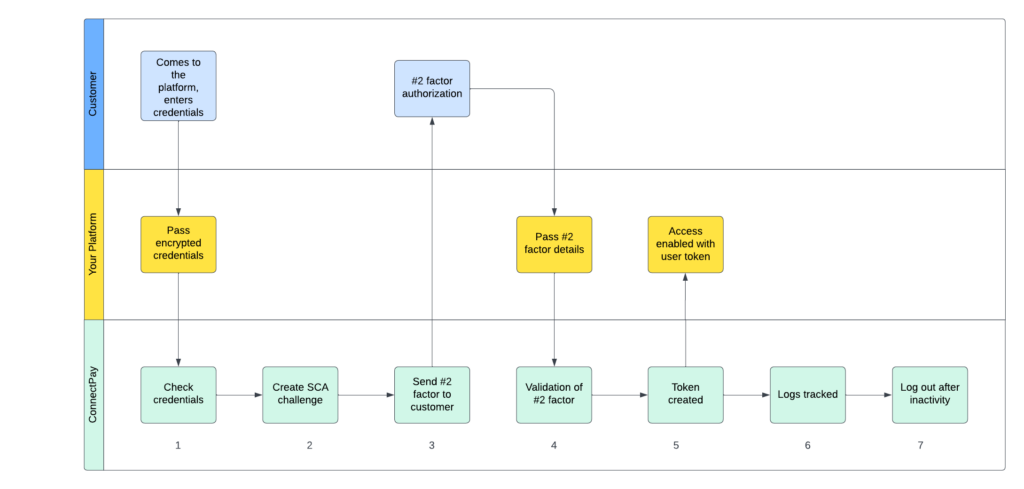
Based on 2 different approaches, in the table below, we provide a comparison between them:
| Step | Benefits (Own Implementation) | Challenges (Own Implementation) | Benefits (ConnectPay) | Challenges (ConnectPay) |
|---|---|---|---|---|
| 1- Credential creation and validation | – Customizable credential selection | – Managing user database | – Password encryption done by ConnectPay | – Credential validation based on ConnectPay processes |
| 2 – SCA factor creation | – Freedom to choose the second factor | – May require external vendors | – Integrated with ConnectPay BaaS APIs | – Only SMS OTP is available |
| 3 -Sending second factor to customer | – Customizable messages | – Defining SCA-required events ; – Dynamic linking | – Dynamic linking done by ConnectPay | – ConnectPay name visible in SMS sender |
| Validation of second factor | – Custom validation processes | – May require external vendors | – Validation handled by ConnectPay | – None |
| Enabling access | – User activity tracking | – Ensuring the session short-lived | – Token provided by ConnectPay | – User token management |
| Logging | – Detailed logging | – Logs must be saved for 13 months | – No need to save logs | – None |
| Terminating a session | – None | – None | – Session termination after token expiry | – Implementing refresh session flow |
Recommendation
Ultimately, the choice of the Strong Customer Authentication method lies with you. It’s essential to consider the needs of your business, the expectations of your customers, and the regulatory requirements. By evaluating the balance between security, user experience, and operational efficiency, you can confidently implement a solution that supports both compliance and customer satisfaction. This decision is not just about meeting today’s standards but about building trust and security for the future. Thus, ConnectPay offers flexibility for a partner to use the approach that best fits their needs.